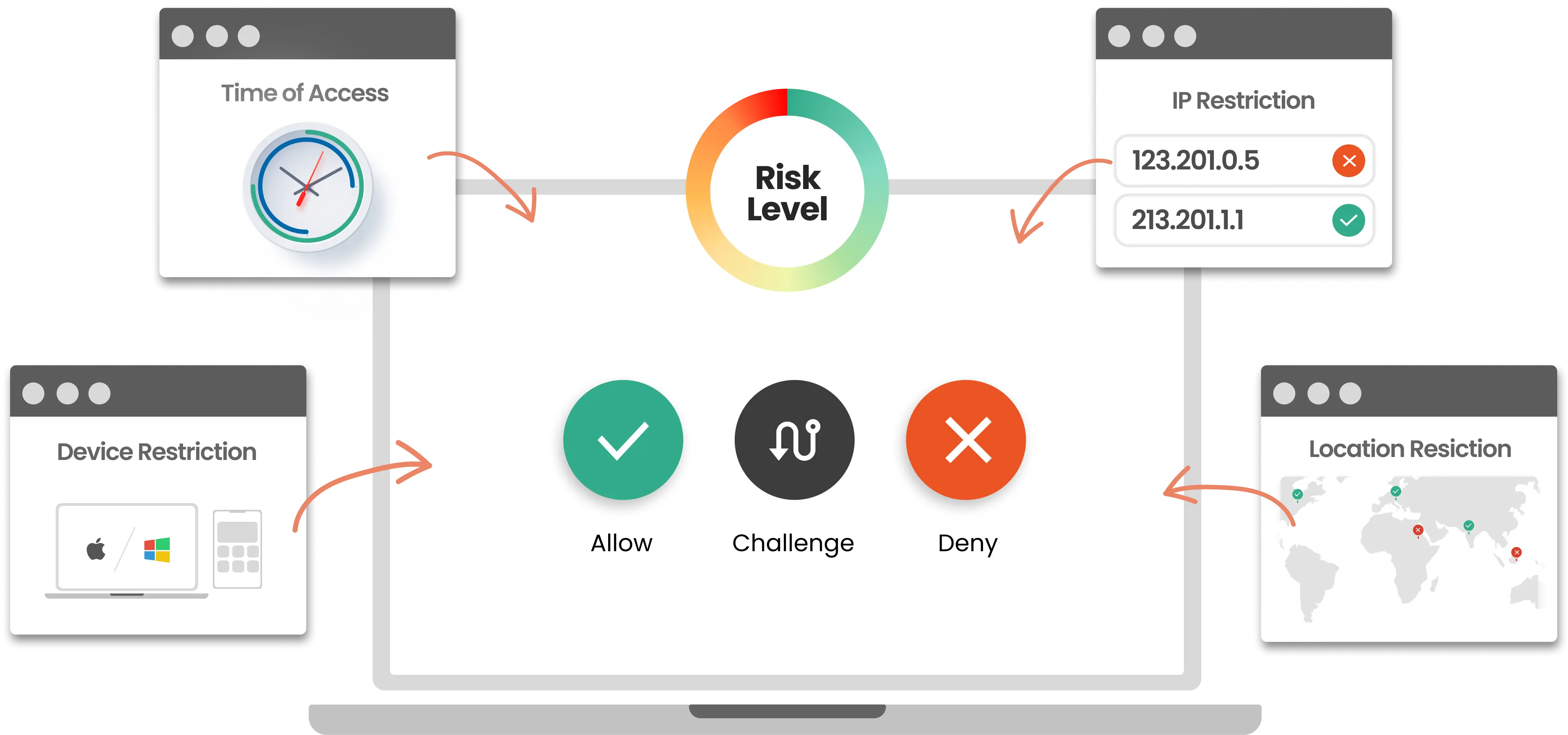
Risk-Based Authentication: The Future of Workplace Security

What is two-factor authentication?
What Is a User Authentication Policy? - Cisco
Secure Authentication - Everything You Need to Know
Authentication in E-Commerce - Transmit Security
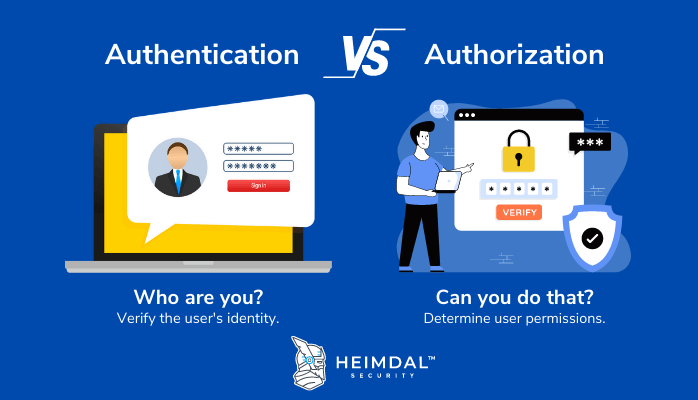
Authentication vs Authorization: What Is the Difference Between Them?

8 Authentication Methods that Can Secure the Different Industries

User Authentication Methods - Fully Verified

The Importance Of Password-based Authentication

Identity Authentication Service in a Nutshell
